
Network Packet Broker
Network Packet Broders operate by gathering network packets from various traffic sources (physical, virtual and cloud). Aggregation, filtering and regeneration of traffic from different sources and sending only relevant data to the monitoring tools
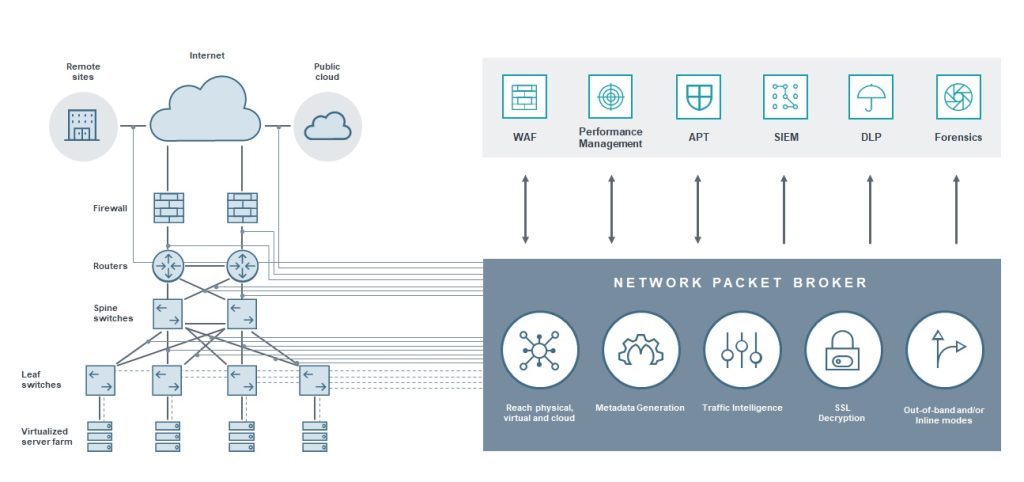
Network Packet Broker Top Use Cases
Pain Point:
- Contention for SPAN ports delays critical projects
- Organizational barriers make it difficult to access network data
- Poor reliability of SPAN data
- Few tool ports but many switches
Solution:
- Pervasive and reliable data access with Network Packet Broker
- TAP instead of SPAN
- Filter relevant data from anywhere in infrastructure using the Network Packet Broker filtering function and deliver to tools
- Feed data to multiple tools simultaneously
Pain Point:
- Unnecessary and expensive security/monitoring tool upgrades due to network upgrade
- Ad hoc deployment of tools provides partial visibility
- Tool overload due to excessive traffic from network upgrade
- Network speeds and tool capacity do not match
Solution:
- Abstraction with the Network Packet Broker. Select traffic of interest using traffic maps
- Network Packet Broker Traffic Intelligence to optimize tools' performance (e.g de-duplication, slicing, NetFlow generation)
- Filter relevant data from anywhere in infrastructure using the Network Packet Broker filtering function and deliver to tools
- Network Packet Broker supports speed conversion between network data source ports and tools ports
Pain Point:
- Tool overload due to increased monitoring traffic
- Speed of upgraded network and tools' monitoring interfaces do not match
Solution:
- Network Packet Broker supports load sharing of monitoring traffic to a group of tools; tools resilience can also be achieved
- Tool's expansion can be achieved through scaling out by Network Packet Broker. ROI for expensive tools much improved
Pain Point:
- Lack of visibility and control of growing SSL/TLS traffic and applications causes blind spots
- Inability to expose and mitigate SSL-based malware and data exfiltration
- Performance degration when enabling SSL decryption in existing security tools like NGFWs
Solution:
- Network Packet Broker supports out-of-band SSL decryption for inbound traffic to internal servers
- Network Packet Broker supports inline SSL decryption for outbound traffic to external servers
Pain Point:
- Blind spots in east-west application traffic
- Visibility and Security gap when applications scale out (new VMs spun up)
- Security tools unable to process encapsulation protocol (e.g VXLAN)
- Lack of flow summaries for analysis tools
Solution:
- Traffic within virtual infrastructure can be tunnelled to centalized out-of-band tools
- API integration with VMware NSX: automatically associates visibility policy to new spun-up VMs
- De-capsulate VXLAN traffic (remove headers)
- Centralize Netflow generation from Network Packet Broker
Network Packet Broker Key Intelligent Features
Traffic Filtering, Aggregation and Regeneration
Traffic Filtering, Aggregation and Regeneration
Core capability of Network Packet Broker to allow only relevant data is sent to network monitoring and security tools, in any-to-any fashion
Packet De-duplication
Packet De-duplication
Remove duplicated packets due to SPAN characteristics or tapping from multiple chained segments. This helps eliminating tools performance bottleneck
Header Stripping
Header Stripping
When traffic is collected from inter-switch links, packets may have additional tags, labels and protocol encapsulation. Stripping operation allow tools access to unreadable traffic
Load Balancing
Load Balancing
Load balancing can optimize tools performance by distributing traffic load evenly. Besides, tools expansion can be easily scaled out with resilency
SSL Decryption
SSL Decryption
Decrypted monitoring data can be forwarded to multiple network monitoring tools like IPS, IDS, protocol analyzers, SIEMs tools, etc
Timestamping
Timestamping
Hardware based timestamp can facilitate troubleshooting for timing problems such as application response time, jitter and latency
Packet Slicing
Packet Slicing
When using packet slicing, the frame headers are kept, and the payloads dropped. By removing payloads that are irrelevant, tool storage usage can be reduced significantly
Netflow Generation
Netflow Generation
Transforms packet data into summarized Netflow records to empower visibility for flow-based security solutions. Besides, non-sampled Netflow can be generated to offload network equipment burden
Data Masking
Data Masking
Packet Brokers can obfuscate sensitive data to comply with privacy regulations
