
Flow Based Network Detection and Response
Tapping into your existing infrastructure to provide comprehensive visibility and detection across your entire IT environment. With dynamic ML behavior baselining, Plixer allows you to detect threats early and at every stage of an attack
Read More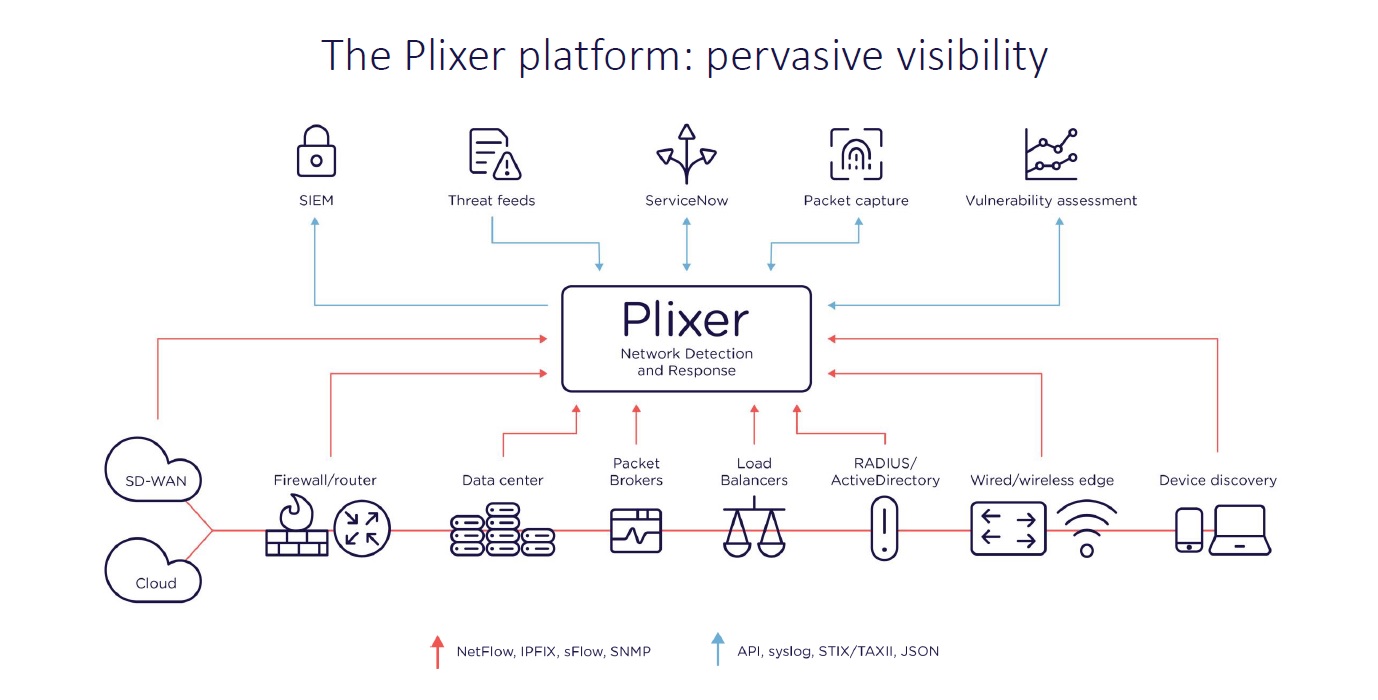
Plixer One Key Benefits
We’ve been innovating and delivering proven, cutting-edge NetFlow/IPFIX-focused technology solutions for over 20 years. IPFIX is a broadly adopted IETF protocol standard, eliminating the proprietary lock-in of other vendor solutions
Shift from passive preventive measures to a dynamic approach. Utilize contextual forensic data to support faster time-to-issue-resolution. Set proactive thresholds and alarming to enable rapid event response
Correlate and consolidate traffic flows and metadata into a single database to cut through noise and focus monitoring where it matters most
No need for intrusive, costly and proprietary network appliances - Plixer’s implementation collects data available directly from your existing IT infrastructure
Plixer One Security
Detect and track threat actor movement
Get early detection of a threat actor’s movement throughout the network. A dynamic activity baseline gives you early alerts on abnormal network traffic behaviors (i.e., worm detection, NetBIOS, and Kerberos abuse behaviors). See lateral movement, command & control, and more all mapped to a MITRE ATT&CK® framework for quick prioritization
Track suspicious data activity
Detect a threat actor staging, collecting, or exfiltration of data. Get alerts on unusual device behavior. See events mapped to MITRE ATT&CK® framework for quick investigation and response. Dig into device communications, finding frequency, duration, locations, and more
Malware and ransomware detection
Detect a threat actor infiltrating devices on the network. Establish and visualize a dynamic baseline for network behavior. Detect activity that falls outside that baseline. Use AI/ML, STIX/TAXII, and threat intelligence feed to correlate activity to malware and ransomware
Device discovery, profiling, and risk scoring
Gauge overall endpoint risk with a concise, aggregated score. Determine the risk of devices by calculating operating-system-related risks, device-related risks, communications-related risks, and risks identified by external endpoint management/security solutions. Endpoint risk scoring alerts you to risky devices and devices that are not on a current OS
Advanced DNS monitoring
Monitor DNS activity and block access to suspicious pages and servers. Monitor, correlate, and analyze DNS requests from all devices and block suspicious requests. Detect DNS activity associated with ransomware, malware, command and control, and data exfiltration. Supplement DNS monitoring by integrating your TAXII server to watch for and block suspicious URL and IP IoCs activity
Cloud visibility and detection
Bridge visibility between on-prem, cloud, and hybrid environments. Plixer ingests flow logs without deploying probes or reconfiguring cloud networks. Visualize intra-cloud traffic, as well as traffic entering or leaving cloud environments. Apply security algorithms, machine learning, and Deep Learning to cloud traffic
Threat hunting
Use network data to proactively uncover threats. Get centralized enterprise-wide traffic data in a single platform. Analyze device-level behavior and dig into thousands of data points. Look through historical data and identify Indicators of Attack (IOA). Use STIX/TAXII feeds to detect suspicious behaviors
Detect insider threats
See suspicious behavior from users with trusted access. Identify anomalous behavior associated with specific usernames. Spot asymmetrical communications and low and slow patterns. See unauthorized activity with policy validation and compliance reporting. Use STIX/TAXII feeds to detect suspicious behaviors
Policy validation and compliance
Ensure network and security policies are in place and being followed. Gain visibility of established policies and alerts on violations. Determine the best course of action to resolve policy violations
Plixer One Network
Digital experience monitoring
Gain end-to-end contextual visibility into every conversation from layers 2-7. Use AI/ML to proactively plan capacity, and align investments with business needs. Dig into historical forensics to root-cause issues and ensure optimal user experience
Predictive planning
Plan for capacity changes, infrastructure upgrades, or cloud migration. Use ML to create a dynamic baseline for network behavior. Extend any Plixer report into the future to forecast trends and predict changes to network behavior
Anomaly detection
Get early detection of traffic behaviors that may cause network issues, interruptions, or outages. Establish and visualize a dynamic baseline for network behavior. Get alerts on activity that falls out of the usual traffic patterns. Customize thresholds for accurate alarms
Device discovery, profiling & risk scoring
Gauge overall endpoint risk with a concise, aggregated score. Determine the risk of devices by calculating operating-system-related risks, device-related risks, communications-related risks, and risks identified by external endpoint management/security solutions. Endpoint risk scoring alerts you to risky devices and devices that are not on a current OS
Cloud visibility and detection
Bridge visibility between on-prem, cloud, and hybrid environments. Plixer ingests flow logs without deploying probes or reconfiguring cloud networks. Visualize intra-cloud traffic, as well as traffic entering or leaving cloud environments. Apply security algorithms, machine learning, and Deep Learning to cloud traffic
Policy validation and compliance
Ensure network and security policies are in place and being followed. Gain visibility of established policies and alerts on violations. Determine the best course of action to resolve policy violations
